

Last updated on

Several users have reported that the latest version of WordPress is causing trojan alerts, and at least one individual mentioned that their web host restricted access to their site due to the file. This situation ultimately became a valuable learning experience.
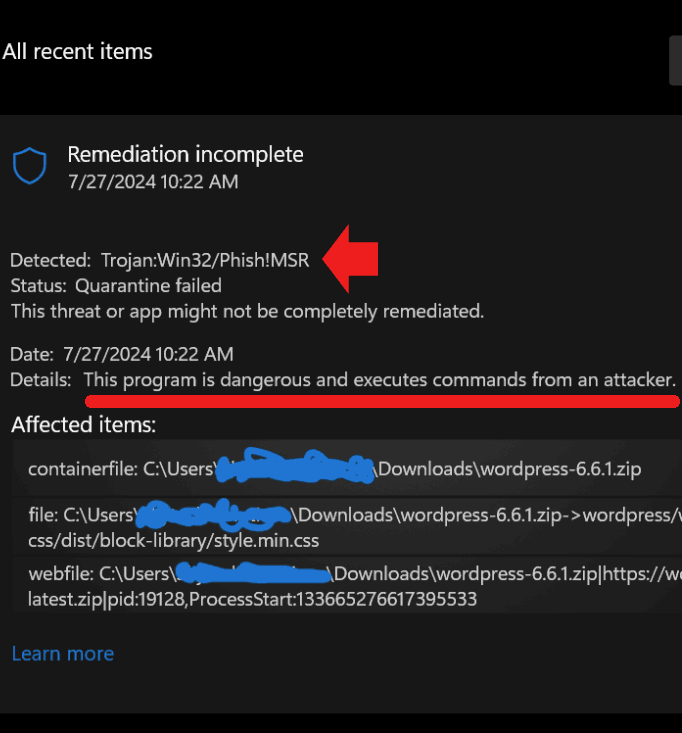
The initial report appeared on the official WordPress.org help forums, where a user claimed that Windows Defender, the built-in antivirus in Windows 11, flagged the WordPress zip file they downloaded from the official site as containing a trojan.
Here is the original post:
“Windows Defender is detecting the latest wordpress-6.6.1.zip as Trojan:Win32/Phish!MSR when I download it from the official WordPress site. The same virus alert appears when updating from the WordPress dashboard of my site. Is this a false positive?”
The user also shared screenshots of the trojan warning, which indicated that the quarantine attempt had failed and labeled the WordPress 6.6.1 zip file as “dangerous” and capable of executing commands from an attacker.
Another user confirmed they were encountering the same problem, identifying a specific string of code in one of the CSS files (which controls website appearance, including colors) as the source of the warning.
They posted:
“I’m having the same issue. It seems to be related to the file \wp-includes\css\dist\block-library\style.min.css. A particular string in this CSS file is being flagged as a Trojan virus. I’d like to permit it, but I think I should wait for an official response first. Can someone provide an official answer?”
A false positive occurs when a test incorrectly indicates the presence of something that isn’t actually there. WordPress users soon began to suspect that the Windows Defender trojan virus alert was a false positive.
An official ticket was filed on WordPress GitHub, which identified the issue as an insecure URL (using http instead of https) referenced within the CSS stylesheet. Since URLs are not typically part of a CSS file, this may have led Windows Defender to flag the CSS file as containing a trojan.
Here’s where things took an unexpected turn. Another WordPress GitHub ticket was opened to address the insecure URL, which should have resolved the issue. However, this led to a deeper investigation and new discoveries about what was actually happening.
The insecure URL in question was:
http://www.w3.org/2000/svg
The person who opened the ticket updated the file to include a link to the HTTPS version, which should have resolved the issue. However, a key detail was overlooked.
The so-called ‘insecure’ URL wasn’t a link to external files (and therefore not actually insecure). Instead, it was an identifier used to define the scope of the Scalable Vector Graphics (SVG) language within XML.
Ultimately, the problem wasn’t with the code in WordPress 6.6.1, but rather with Windows Defender misidentifying an “XML namespace” as a URL linking to downloadable files.
The false positive trojan alert from Windows Defender and the ensuing discussion served as a valuable learning experience for many, including myself, about the often-overlooked details of XML namespaces in SVG files.
Original news from SearchEngineJournal